Navigating the Web Anonymously: The Function of Proxy Servers

In digital landscape, online privacy and security have become essential concerns for individuals and organizations alike. With the growing threats of information leaks, monitoring, and spying, many are turning to proxy servers as a solution for navigating the web privately. But what is a proxy server, and how does it work? At its core, a proxy server acts as an intermediary between your device and the internet, allowing you to access online content while hiding your IP address. This not only helps in safeguarding your personal information but also enhances your online experience by providing access to geo-restricted content and improving browsing speed.
As you delve further into the world of proxies, you will find various types, each designed for specific needs, ranging from simple web browsing to complex data scraping and market research. Understanding the advantages and potential risks associated with different proxy types is crucial for anyone looking to enhance their online security and privacy. Whether you are a business looking to protect sensitive information, a gamer looking to reduce latency, or simply a user wanting to keep your browsing habits secret, this article will guide you through the essential aspects of proxy servers and how they can improve your online footprint.
Understanding Proxy Servers Servers
Proxy servers function as middlemen between your device and the internet. As you connect to a proxy server, your inquiries for web content are initially routed through the intermediary rather than going straight to the specific website. This implies that the website sees the proxy's IP address instead of your own, providing a level of anonymity and secrecy. By masking https://omeka.net , proxy servers can help keep your online activities more protected and confidential.
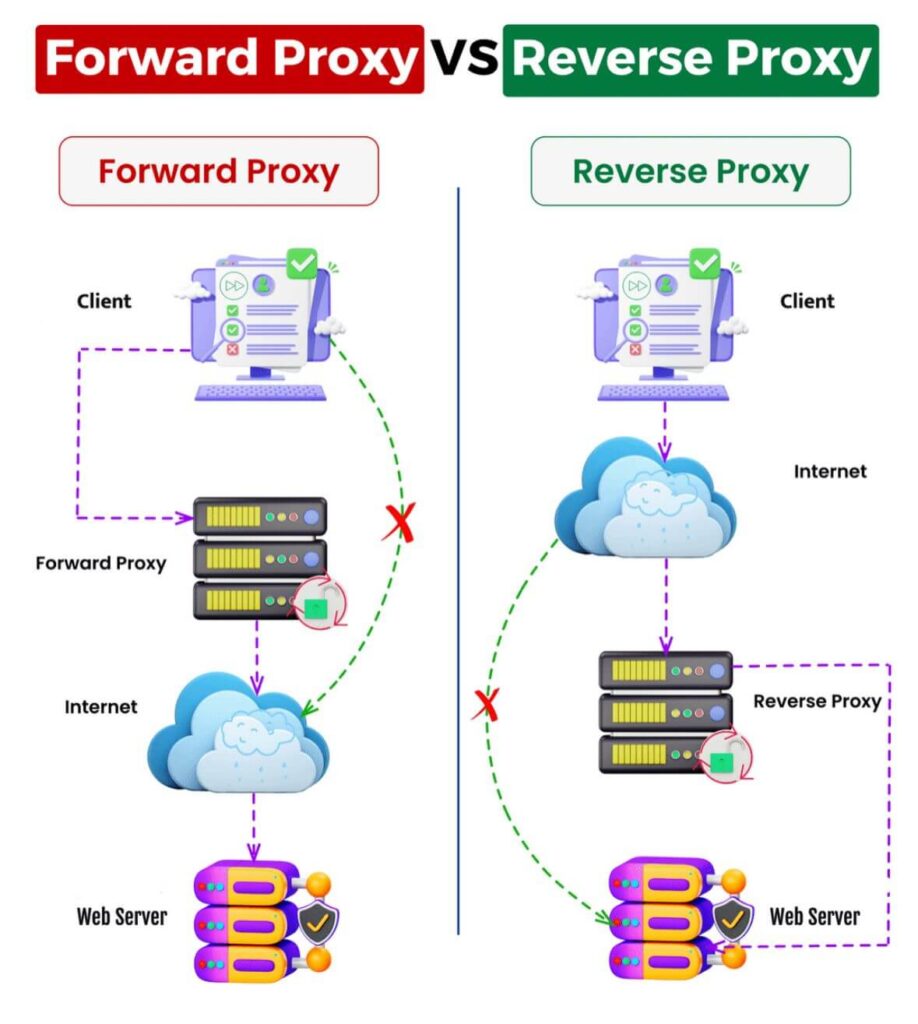
There are various kinds of proxies, such as HTTP, SOCKS, and transparent servers, each fulfilling specific functions. HTTP proxies are designed for web browsing, while SOCKS proxies can manage multiple types of data. Transparent proxies, on the contrary, do not alter inquiries and can be employed for content filtering. Comprehending these types helps users choose the suitable proxy for their requirements, whether it be for anonymity or functionality.
The benefits of using a proxy go beyond anonymity; they can also improve safety, boost online secrecy, and bypass geo-restrictions. For individuals, this means accessing content that may be restricted in their area. For companies, proxy servers can strengthen cybersecurity by protecting against data breaches and reducing the chance of exposure to harmful attacks. By integrating proxies into their online activities, users can browse the web with greater confidence.
### A Comparison of Proxy Servers and VPNs
As you evaluate methods for enhancing online privacy and security, numerous users find themselves weighing the pros and cons of using VPNs versus proxy servers. Proxies serve as intermediaries between the user and the internet, channeling requests through an alternative IP address, helping to conceal the identity of the user. However, they usually fail to provide encryption for traffic, so even if users attain a certain level of concealment, their data might still be susceptible to interception by third parties. On the other hand, VPNs leverage encryption to safeguard the user's information, offering a more thorough solution for privacy and security, particularly for accessing sensitive data.
A further notable difference lies in the level of functionality available with each choice. Proxies prove beneficial for specific tasks such as overcoming geographical restrictions, accessing blocked content, or content extraction. They may offer better speeds than VPNs since they lack the encryption overhead. However, they typically miss out on strong security measures that VPNs provide, making them less suitable for those wanting to protect their online activities from threats. VPNs offer greater versatility when it comes to protecting data across various applications and devices, beyond just web browsers, which expands their usefulness for individuals wary of their complete digital presence.
In conclusion, the decision between a proxy and VPN will depend on individual needs and use cases. For those mainly focused on privacy while surfing or navigating particular websites, proxy servers may be adequate. However, for those seeking an all-encompassing solution that provides high levels of security and privacy, a VPN is probably the superior choice. Understanding these distinctions can help users make informed decisions tailored to their online behaviors.
Benefits and Threats of Employing Proxies
Employing proxy servers delivers multiple advantages for people and organizations aiming to improve their internet privacy and security. One of the primary benefits is privacy; by routing your internet traffic through a proxy, your actual IP address is obscured, making it harder for websites and online services to track your activities. This can be particularly beneficial for people concerned about their online footprint or potential data breaches. Additionally, proxy servers can assist users get around geo-restrictions, allowing entry to content that may be restricted in certain regions, thus expanding the range of internet resources accessible.
However, there are risks associated with using proxies, particularly free ones. Many free proxies may not provide sufficient protection, leaving users exposed to data interception and malware. They could log your browsing habits and expose your personal information to third parties. Moreover, certain proxies can in fact reduce your connectivity speed or lead to unreliable connectivity, which can hamper your internet experience. It’s crucial to exercise caution and select reputable proxy services that prioritize user security and confidentiality.
In business environments, while proxies can improve productivity and security, improper management can lead to potential risks. For example, poorly configured proxies may result in sensitive information leaks or unapproved access to confidential data. Businesses must carefully evaluate their proxy options to ensure that they are creating a secure network environment without inadvertently risking their systems to threats. Finally, grasping both the advantages and risks is essential for making wise choices about integrating proxy servers into your online activities.
