Discovering the Power of Proxy Services: A Thorough Guide

In the current digital landscape, confidentiality and safety have become paramount for internet users. As we navigate through a myriad of online threats and restrictions, grasping tools like proxies can considerably enhance our online experience. Proxy servers function as intermediaries between your device and the internet, providing numerous benefits such as anonymity, entry to geo-restricted content, and improved security. This comprehensive guide aims to unveil the power of proxy servers, exploring how they work, their various types, and the advantages they can provide in both personal and professional settings.
Whether you are a casual user seeking to maintain your privacy online, a business seeking to bolster your cybersecurity measures, or a gamer wanting to reduce lag, proxy servers can serve a vital role in achieving your goals. We will explore the nuances of using proxies, discussing aspects such as their role in data scraping and market research, their effectiveness in accessing content, and the risks associated with free proxies. With this knowledge, you can make informed decisions about utilizing proxy servers to enhance your online safety and productivity.
Comprehending Proxy Server Systems as well as Their Functionality
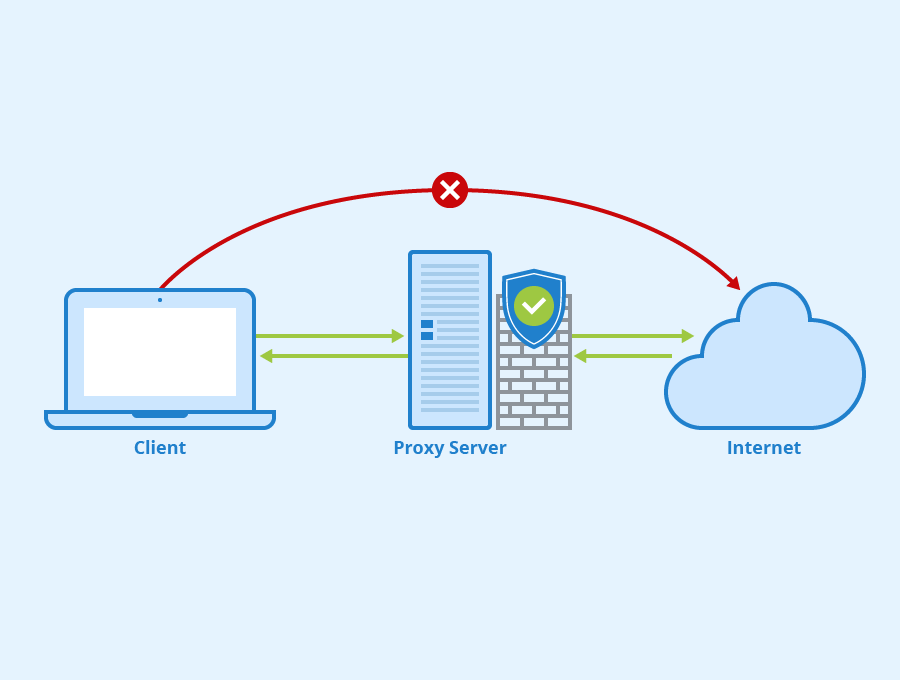
A proxy server serves as an intermediary between a user's device and the internet. When a user makes a request for a web page, the proxy server transmits the request to the target server. The target server then returns the sought data back to the proxy, which ultimately relays it to the user. This process helps mask the user's actual IP address, providing a layer of privacy and discretion. By doing so, proxy servers enable users to browse the web without exposing their location or identity to the sites they view.
Proxy servers come in multiple types, all created for specific functions. Some frequently encountered types are HTTP proxies, SOCKS proxies, and transparent proxies. HTTP proxies are usually used for web traffic, while SOCKS proxies provide for a wide range of protocols. Transparent proxies can filter content without changing requests or responses, often used in corporate environments to implement policies. Each type serves distinct functions, permitting users to choose the most suitable choice based on their needs.
Understanding how proxy servers operate is essential for utilizing their full effectiveness. Not only do they boost online security, but they also enable users to obtain geo-restricted content and overcome network restrictions. For businesses, proxy servers can improve security by managing network traffic and preventing unapproved access. Overall, these servers are versatile tools that significantly affect how individuals and organizations engage with the digital landscape.
Advantages and Risks of Using Proxy Servers
Proxies offer numerous benefits for users seeking improved online privacy and security. One of the main advantages is the ability to mask one's IP address, making it much more difficult for websites and malware entities to track online activities. This added layer of anonymity helps protect personal information from being harvested, especially in environments where privacy is a issue. Additionally, proxy servers can improve internet performance by storing frequently accessed content, thus reducing loading times and improving the overall browsing experience.
On the contrary, not all proxies come with the same standard of security and reliability. Free proxy servers, in particular, pose significant risks, such as data interception and malware exposure. Many free proxies are run by anonymous entities, raising concerns about how they handle user data and whether they monitor online behavior. Users can expose themselves to multiple threats, including the potential for hacking or identity theft, if they are not careful about the type of proxy they choose.
Additionally, the legal and ethical implications surrounding the use of proxy servers cannot be dismissed. Some services, such as streaming platforms and sites, actively block access through proxy servers, leading to frustration for users who seek to bypass geo-restrictions. Additionally, using proxies for web scraping can walk a fine line, as it may violate the terms of service of multiple websites. Understanding these risks is crucial for users to make educated choices about their online activities and ensure they are using proxies correctly.
Proxy in Different Use Cases
Proxies serve a wide range of functions across various sectors. For businesses, they are essential for enhancing cybersecurity by acting as a shield between users and dangerous sites. By filtering content and tracking web traffic, proxy servers can help prevent data breaches and unauthorized access. Additionally, they provide anonymity for individuals, making it difficult for threat agents to track individual activity. This is particularly crucial in environments where sensitive data is handled.
In the realm of online privacy, individuals often utilize proxy servers to protect their identity while browsing the internet. By routing their connection through a server, users can mask their IP address, making it seem as if they are accessing the internet from a varied location. This is especially beneficial for those who want to maintain their privacy on public Wi-Fi networks or access region-locked content, such as media platforms that might block users from certain regions. The use of proxies in this way can enhance personal security and access to global content.
Another significant use case for proxy servers is in data scraping and market research. Companies leverage proxy servers to gather data from various online sources without revealing their identity or facing potential blocking. By rotating https://buyproxy.omeka.net/ through a network of proxy servers, organizations can continuously collect data, monitor competitors, and analyze market trends without detection. This capability is invaluable for companies looking to stay ahead in today's competitive landscape, illustrating the diverse applications of proxies in both commercial and personal contexts.
